The Internet is a dangerous place. Especially if you are LGBTQ, furry, have unconventional sexual tendencies (CNC, BDSM, FinDom, etc) or are a member of a religious or racial minority group.
The Internet was not designed with safety or security in mind. In its ARPANET beginnings, many systems didn’t even have passwords because only privileged users were supposed to access them. As such, privacy and security features are often little more than layers added on top of aging protocols, like HTTPS is just SSL applied on top of HTTP.
As such, the Internet has, for years, consisted of open access, anonymity, and censorship resistance at the cost of privacy and security.
Nowadays, threat actors, law enforcement and national intelligence agencies, defence contractors, private investigators, hate groups, and analytics corporations (and more recently, AI bots and AI corporations) scan, monitor, and scrape the Internet, collecting gargantuan amounts of information, to aggregate using Big Data and analysis techniques for all kinds of purposes, including anti-terrorism operations, doxxing, trolling, and harassment, or market analysis.
Staying safe: Generic tips
Regardless of the platform, there are a number of measures you can take to make it more difficult for anyone to identify you online.
Threat modelling
Who do you want to defend yourself against? The NSA? GCHQ? Good luck with that. If you are notorious enough, and do crimes or become an interesting target for a government-funded agency, no amount of VPNs, Tor proxies, and PGP keys will protect you. If you become a National Security threat, you are highly unlikely to escape the grasp of government agencies.
If, on the other hand, your plans are more modest and involve protecting yourself and your family, your finances, possessions, and other things against nosy neighbours, ex-partners and current and future employers, then it is a much more doable task.
Who are you? Do you belong to a minority? Are you an immigrant, or LGBT? An activist, or a journalist? Do you have a lot of money? These are important questions. Who would be interested in your personal information specifically? Advertisers? Cybercriminals? Scammers?
You must understand what their techniques are. Receiving a Nigerian Prince phishing e-mail is totally different to a creepy, jealous ex-partner looking at your Twitter feed with a secondary account. Use this knowledge to try to deploy the appropriate countermeasures.
This post will not help safeguard your accounts and digital presence against government-sponsored threat actors, because I consider it a fruitless endeavour: If you are notable enough, you will not be able to escape the government. And if you are not notable enough, then they won’t bother tracking you down, because it is a colossal waste of resources. But it will give you tips on how threat actors operate and how to be safer online.
Ego is the enemy
The most important tip of all is to understand your ego, and yourself. One common pitfall I see frequently, especially among teenagers and less tech-savvy individuals is they enjoy attention and notoriety. This is nothing to be ashamed of or ridiculed for, as it is a fundamental part of what makes us human. We crave connection and socialising, and social people develop healthier brains. But you must also balance this craving for notoriety and socialisation with the dangers of inadvertently exposing yourself on the Internet. And I think a big part of this is about one’s ego. Social networks play with our instincts by giving us small dopamine rewards in the form of view counters, likes, retweets, and other forms of attention. Once you understand how perversely manipulative these incentives are, you can begin to rethink your approach to social media. My recommendation is to disable as many non-direct interaction notifications as possible. For example, whenever I can, I disable reaction notifications: those small emojis that can be applied to other people’s messages. They do not convey much information other than approval / disapproval. I also disable likes and retweets in platforms like Twitter. Again, these notifications serve no purpose other than telling your brain “look, you did something other people liked” which in turn tricks you and makes you feel good for a short while. Same goes for messages in group chats like WhatsApp or Telegram: You do not need to be notified every time anyone sends a message to a group. You do need to get notified if other people address you specifically, via mentions or something similar.
Generally, I recommend disabling every single interaction that is not clearly addressed towards you. Usually this includes e-mails as well, because it is common to be on several marketing and newsletter e-mail lists, and it is rare to receive e-mail messages addressed to you specifically, however, in my case, I aggressively unsubscribe and block any source of unsolicited messages, so all my e-mails are addressed to me, or are notifications like bills and other things I really need to be aware of, so my e-mail notifications are always on.
Phone numbers
Phone numbers are often one of the least protected pieces of information online. First of all, they’re not directly traceable back to a specific person, however, in many countries, there are “White pages” services that allow you to link a person’s real name with a phone number. You might even be listed there without your knowledge! It’s important to opt out. Each country has a different procedure, and often times it is your phone service provider who signs you up. Simply search “White Pages <your country>” and figure out how to opt-out. Also talk to your phone service provider / ISP / carrier, and ask them to de-list your information from any public sources. EU GDPR and California’s CCPA laws, among others, might have specific opt-out mechanisms. Make sure to exercise your legal rights!
Do not give out your phone number
Be wary of any website or service asking for your phone number. These websites will often try to convince you to give them your phone number with the pretext of “increased account security”, or “to facilitate recovery”, or even “to send you updates regarding your order”. Please understand that they will often sell this information to advertisers and intelligence agencies. Even when they promise not to sell their data, they might get hacked one day. You might not even know they got hacked. Do you often receive robocalls? Maybe your phone number got leaked or sold.
Always use Google Authenticator*, Security Keys, and other Two-Factor authentication mechanisms, instead of SMS.
* Note: When I mention Google Authenticator, I am specifically referring to RFC 6238. Google Authenticator is the most well-known implementation, but alternatives exist. Check out Aegis Authenticator (open source), Ente Auth (open source with cloud sync), or Authy (not open source, with cloud sync).
In most extreme cases, websites like Gmail will require you to attach a phone number to your account in order to register. Otherwise, you cannot create an account, or your account will be deactivated under suspicion of fraud or automated spam. In this case, it is important to consider if you really need access to that service. Sometimes, using a VPN service and switching countries to those with better privacy laws like Switzerland or Netherlands might help. Otherwise, the use of a VPN might paint an even bigger target on you, as VPN IP addresses are well-known to certain groups and agencies.
Giving out your phone number can also make you vulnerable to many flaws in telecommunication systems.
An alternative to real phone numbers is to use VoIP/eSIM phone numbers from silent.link, sms4sats, or eSIM.me.
SIM swapping
Cybercriminals and threat actors can trick your carrier into giving them your SIM by doing some research on you, then posing as you to them via customer service lines. Customer service employees are often overworked or underpaid, and therefore they are highly vulnerable to being manipulated, as they won’t have much motivation to implement strict safety measures. Another technique is by using an insider: you pay your insider, and they generate a new SIM for you, transferring your phone number to them. From this point onwards, they can spoof your calls, request Two-Factor authentication SMS tokens, or even call your bank or relatives, tricking them into sending money, from a very familiar phone number using voice changer software.
SIM privacy laws
Countries increasingly require SIM-card registration. The rationale behind this is often along the lines of counter-terrorism and avoiding cyber-stalking and harassment. I’m not going to argue one way or another, but the fact is if you ever gave out your personal information in order to obtain a SIM card, that automatically means there exists a database somewhere, where your name and phone number are related. It may be better or worse protected, but if that information is ever exposed, you could be in danger of identity theft, fraud, and more. Be aware of this whenever any website or app asks you for your phone number. Especially those messaging apps like WhatsApp or iMessage that share your phone number with all your contacts.
Public posts
Due to the basics of Information Theory, it is not possible to guarantee deletion of any piece of data in computer systems. In other words: that “delete” button next to your tweets might not do what you think it does.
Same happens with your computer files. In old hard disk drives, data is not deleted even when you use the “delete” command in your operating system. Data is stored in regions, and those regions are marked as deleted. This is an important distinction, because, for performance reasons, this data is not actually removed, but the space held by the data becomes available for later use. A similar situation happens with solid-state disks. In this case, it is also for longevity reasons, because every time you write data to a solid-state disk, you reduce its life expectancy. These devices have limited writes, and the controller that takes care of sorting this information is responsible for marking cells deleted, without actually removing the data.
There are many other cases. For example, when you send data over two computer systems, it is often the case this data will, at some point, reach a router, a switch, or another intermediary device. This device will then store the data, and then send it again towards its destination. At this point, there is no guarantee that this device hasn’t stored a copy of the data exchanged. So even if the data is deleted and both the receiving as well as the sending systems are destroyed beyond recovery, there can be perfect copies of this data stored somewhere. This is the basic principle for executing MITM attacks.
Thus, you should assume any data you have ever posted in a public setting, like a group, a newspaper, a blog, or unencrypted mediums like e-mails to be susceptible to being stored permanently without your consent or knowledge.
Do not simply assume the delete button will make your tweet no longer accessible. Free tools like archive.org can help you see previous versions of websites, allowing you to recover data that is now deleted or has been modified.
Going on vacation
When going on vacation, it is typical for people to be very eager and share pictures of their trip shortly after they’re taken. Sometimes, even livestreaming their vacation. This poses all kinds of risks, not only because people can guess where you are, but also because people can guess where you aren’t. For example,if you work at a well-known company, knowing that one of the employees are on vacation is highly valuable information in case they want to conduct some kind of social engineering attack impersonating you. Or, even worse, if they know where you live, they can just enter your home and rob you, knowing your home is completely unprotected.
Instead of announcing you go on vacation in a public post, and post pictures and videos of your daily occurrences, wait until you return. Once you are home, it is perfectly safe to post pictures (depending on your threat model), as you are no longer in the location where the picture was taken.
Pictures and media posts
You should avoid posting pictures of your face online. Once a picture is posted, it may stay there forever, like it or not. Although this certainly depends on your threat model. For example, if you are a well-known person in your field, it might not be very useful to avoid posting pictures of your face online, as there will likely be pictures of you, sometimes taken without explicit consent.
However, in content that is even remotely controversial or disagreeable, like politics or sexual themes, it is advised to implement a strict separation between normal / professional life and your political opinions or sexual activities.
Public profiles and “bios”
Seek to minimise the amount of information you give out publicly. You can also try giving out false information, such as, for example, setting your date of birth to a different date, or setting your city to another nearby city, or even a different country.
Any bit of information you give out can be correlated with your posts and your social media presence to find out more about you.
Profile privacy
Some platforms like Twitter offer privacy methods in which your account becomes readable only to users who receive your explicit approval. Then, anonymous users and non-approved users can no longer read your posts, but your approved followers can.
Unique usernames used on multiple platforms
Some people choose to have identifiable usernames online. Unless you have a big reason to have a sort of “personal branding”, for example, if you are looking for work and you want to be visible to potential employers, it is probably smarter to generate usernames out of random letters and numbers and never use personal details like year of birth, age, or your real name.
If you do choose to have a “personal branding”, then you must be very careful what you say, or what you post. There’s a lot of information associated to anything you publish online. For example: pictures can sometimes include geolocation data, or people can find out where you are because of geographical features displayed in the picture. The time and date you post can also help locate where you are located in the world, and perhaps even what you do for a living.
Even if you delete your posts, there are tools dedicated to archiving social media profiles including all their posted content.
Online shopping and package delivery
Except in very specific cases, giving out your real name to companies like Amazon or DHL isn’t actually necessary. They will never check your ID. While sending parcels to your home might pose a threat, unless you use sketchy websites, and as long as you never give out your legal name to e-commerce websites, it should be fine.
Usernames and e-mail addresses
Many platforms have a “login” username separate from the name displayed on your profile. Sometimes your login username is just your e-mail address or phone number.
If possible, your username should be never the same in two websites. If your name is “John Doe” and your e-banking username is “JohnDoe”, then that makes it more likely for your banking information to be breached. How about having “dxf15sx4” as username instead? Hard to remember? Yes. You should be using a password manager anyway. In cases like Twitter or Discord where your username is also your social username by which people can reach you, this might not be feasible.
Regarding e-mail, there are some private e-mail service providers. Some people use the “plus-address” trick, but this is not very useful because if your information is ever leaked, anyone knows the first part of your e-mail address, before the + sign, is your real address.
Instead, try completely randomly generated e-mail addresses like abc@yourprovider.com or xyz@yourprovider.com. Do not write your name in the username part of the address. Do not use your initials. Do not make it identifiable.
Some private e-mail providers include:
- https://www.fastmail.com/
- https://simplelogin.io/
- https://33mail.com/
- https://relay.firefox.com/
- https://addy.io/
- DuckDuckGo Email Protection
- iCloud Private Relay
There are of course many more services. Do note that an increasing number of websites will not allow you to sign in using addresses provided by the above services. Some GitHub projects like this one allow you to download a list containing disposable e-mail service providers, as well as the private e-mail providers listed above. A simple workaround is to get a domain name. You can buy a .com domain for less than 10 dollars a year, and then configure your private e-mail provider to use said domain name.
Distrust of people online
It is not wise to trust strangers on the Internet. It is relatively common for things like catfishing, romance scams, or sugar daddy scams to happen.
Scamming techniques evolve continuously and it is hard to keep track of them. But a smart rule to stick to is, if someone on the Internet requests you pay them before delivering any kind of product or service, especially if this individual has contacted you first out of the blue, then it is likely a scam.
But it’s not only scams you have to watch out for. Unfortunately, some people are not scammers but simply bad people.
The cost of betraying your neighbour can be quite high, as your neighbour knows where you live, and possibly the kind of car you drive, or who you are dating. However, on the Internet, things are much more complicated. Even if you talk to someone who you think is your friend, there’s no guarantee they won’t tell other people your secrets. Or worse yet, your friends could be impersonated, or get their accounts hacked.
Privacy VPN services
VPN providers will often sell you the idea of a safer internet with them, but, a VPN is effectively a middle-man between you and the sites you want to visit. Using a VPN means giving all your Internet traffic to this VPN provider, so it is important to make the right choices when looking for a VPN provider. Some VPN providers require and request more personal information than others. Among the most trusted VPN services is Mullvad. There have been cases of VPN providers disclosing information of their users to the authorities in the event of illegal activity, like how HideMyAss helped an FBI investigation when they were served with a court order. In this case, it is hard to argue against HideMyAss, as they are legally required to assist the authorities investigating crimes, but one must also remember that HideMyAss disclosed the information they had on their customers, and this would have not been possible if they had no information on the suspects in the first place.
This guide does not cover threat models that include engaging in crime while avoiding prison or legal consequences but the line between the (legal) right to privacy and criminals using privacy to avoid consequences is blurry at times.
IP Addresses
Depending on how you connect to the Internet, there’s a chance that your IP address is static. This means your IP address never changes, and website administrators can see it. This way, it is easy to track you even across different websites, as they often contain tracking mechanisms from third-party companies like Google or Facebook.
One of the most common ways of dynamic IP assignment happens when your router boots and performs the appropriate handshakes with your ISP. If you are unsure, check your IP using something like ifconfig.me, then reboot your router (power cycle), wait for it to go online, and check your IP again.
Vehicle registration
In some countries, vehicle registration information is easily accessible. In particular, countries like USA, Canada, UK and Australia have weaker privacy laws, and it is possible to retrieve information such as accident history, service and repair records, vehicle make, model, and year.
Tax returns
In some countries, the tax returns are public information, and easy to retrieve, as long as you have the name of the person you are interested in knowing the tax records of. If you live in such a country, you probably know, but the Nordics (Norway, Sweden, Denmark, etc) are famous for this. In some cases, the target person will receive a notification that their tax information was accessed by you, as you have to identify yourself prior to making this inquiry.
So if you live in a country like this, it is easy to estimate a person’s net worth. As such, your threat model should include this consideration.
Credit score and financial information
The US and Canada are notorious for being countries where financial information such as credit score is not particularly well-protected. Landlords, employers, insurance companies and other parties have access to sensitive financial records including credit scores, credit history, bankruptcies, payment history. In most cases, the individual’s explicit consent is required, but this consent, as is the case in other cases, can be forged.
Platform-specific tips
Please note, below I list some unofficial tools. These unofficial tools gaining access to your account could do some serious damage, like deleting groups you own or mass-spamming your contacts. Please exercise caution when running any third-party code.
Emergency Data Requests are legitimate tools for law enforcement agencies to request data on a particular user. This in theory sounds great, because EDRs are only accessible to law enforcement agents, and are a valuable resource in fighting crime. However, in reality, threat actors are known to abuse EDR platforms like Kodex. The method they use to gain access to Kodex is simple: They buy breached government e-mails, like law enforcement agents, government officials, legislators, etc. With this government e-mail, they can then sign up for platforms like Kodex and look up any user they want. These platforms collect vast amounts of information that are then made available via these methods.
Several large platforms like Discord, LinkedIn or Snapchat are available on Kodex. With these, they can then request all the information in a particular account, even data the company promised not to share with advertisers, because companies still have to respect court orders, and (legitimate) EDRs come with court orders.
The generic tips as well as platform-specific tips should hopefully help you maintain a certain degree of privacy.
Do not trust a company to keep your information private. Instead, do your best so that information is never collected in the first place.
Telegram
There are well-known tools like tgScan, and TelegramDB that use various methods to collect membership details in Telegram groups.
These tools are paid, but don’t be surprised if you show up in the search results including all the groups you belong to, or at least some of them.
It is not easy to defend against this because they automate this data collection through bots joining many different groups. However, there’s a few things you can do right now that will increase your privacy.
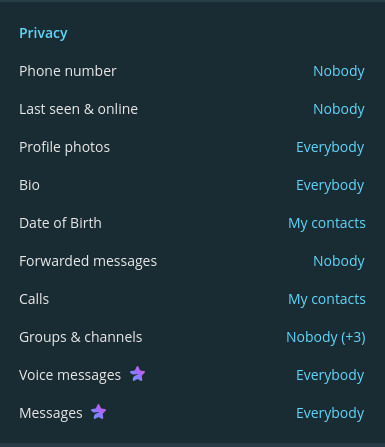
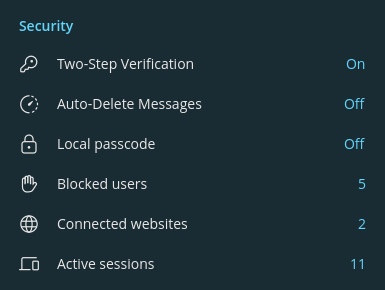
Enable two-step verification
In the security section, you can add an additional password to your account.
This prevents someone else from gaining access to your phone number through SIM swapping or similar and logging into your account, as after entering the SMS code, they will be asked for a password.
Remove your username
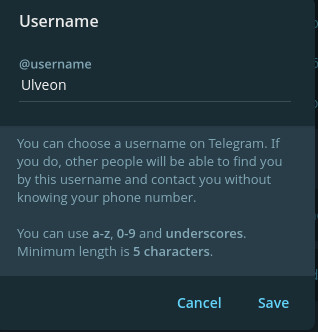
While your account has a user ID attached that you can never change, official clients don’t display it by default, but can be enabled under experimental settings.
If you remove your username, it is not possible for someone else to refer to your account except in the form of mentions in a group chat, or if they manage to get your user ID.
If you have a username set, you can delete the text to remove your username.
Hide your personal details
In settings -> Privacy and Security, you can tune who sees what kind of information about yourself.
I recommend setting the following to “Nobody”:
- Phone number
- Last seen
- Date of Birth
- Forwarded messages
- Groups and channels
A note regarding forwarded messages: People can still forward your messages to other people. The difference is these messages will only carry the name you have set in the app (not your username), and they cannot tap the name to go to your profile as is possible if this setting is configured to “Everyone”.
And, as you can see in the picture (+3), you can add specific people who are allowed to perform certain actions. If your settings are “Everybody”, you can still add exceptions that will not be allowed to, for example see your profile picture or bio.
Enable disappearing messages
In settings -> Privacy and Security, you can enable disappearing messages.
This will make any new private chat (even regular, non-secret chats) have an expiration timer set by you, after which the messages will be deleted for both parties.
The counterparty can always change or disable this expiration timer, but you will be notified if they do.
Mass-deletion of group messages
For this, there are several tools.
I use Nekogram on Android. You can go to each group, and delete all messages, or only messages older than a day or a week.
There are other options, for example, scripts like TgEraser, or wipemychat.
Of course, you should always exercise caution when giving third-party applications access to your Telegram account. They could delete your private messages or even delete groups and channels you own.
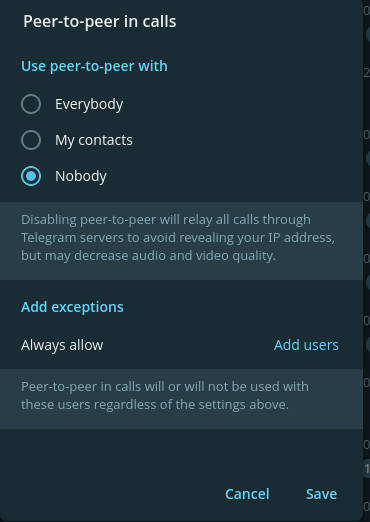
Disable calls
Depending on your security settings, calls can leak your IP address. It is therefore advisable to disable calls, or at least disable peer-to-peer functionality in calls.
WhatsApp doesn’t have a public API, but there are several ways to gather data from a WhatsApp contact. For example, you can use WhatsApp Monitor to stalk anyone given you have their phone number. This allows you to be notified whenever they come online, which means anytime they look at their WhatsApp chats.
DNS / hostnames
DNS can refer to two different things: Registering a domain name, and resolving domain names.
In the case of registration, the standard requires you provide personal information in order to register a domain, this is then possible to retrieve using the WHOIS mechanism. Failure to provide your real details can lead to domain suspension without a chance to get it back. However, legal privacy services exist. In most cases, these hide your PII behind the provider’s infrastructure to protect your privacy. However, your hostname provider is still required to reveal your private information upon being served a court order. These privacy services are often referred to as “WHOIS privacy”.
Even if WHOIS privacy is enabled, DNS records can still reveal information. For example, by checking DNS history records using tools like Passive DNS, investigators can track changes in IP addresses associated with a domain, revealing hosting changes, geographic locations of servers, and patterns of behavior over time.
The second situation is with regards to resolving domain names. In this use-case, DNS is an unencrypted protocol, and this means anyone between you and your target website could potentially learn the kinds of websites you browse to. At a minimum their domain names. To protect yourself in this case, it is possible to make use of encrypted DNS services. Modern web browsers ship with encrypted DNS service providers that bypass OS settings.
To protect your privacy:
- Always opt for WHOIS privacy protection when registering a domain.
- Be mindful of using personal email addresses for domain registrations.
- Consider using DNS providers that offer encrypted DNS (e.g., DNS over HTTPS or DNS over TLS) to limit the leakage of your browsing habits.
Git / GitHub / GitLab
The Git protocol is probably more leaky than you think. The Git protocol requires a username and e-mail address set up in order to make commits. Some git clients and IDEs will auto-generate this based on different parameters. Many git clients take your computer’s username and hostname to generate these fields. This is particularly bad if your computer’s username is your legal name, as this will be visible in any public GitHub or GitLab commits.
Try going to any of my public GitLab repos, go to the list of commits, click the title of any commit, and you will see that my profile is associated with it, including my e-mail address. Git was initially designed to be used through e-mail, and many people are not aware that their e-mail address is attached to every commit they make. If this is sensitive information for you, you should consider an e-mail privacy service that hides your real e-mail address.
There are tools like gitrecon that allow you to download the public SSH keys of a GitLab or GitHub user. With these, you can then correlate accounts if they share the same SSH public key.
Google has an Advanced Protection Program designed to enforce the maximum levels of security and prevent unsafe activities from taking place accidentally. This program is especially designed for people who are under attack from government-sponsored threat actors. Note that signing up to this program will apply limitations to your account, such as:
- You can no longer sign into Gmail using passwords through IMAP / SMTP
- Two-Factor authentication is enforced and you can no longer disable it
- If you sign in with your Google account in an Android phone, you might be prevented from installing certain applications, especially outside the Play Store
Note that the Advanced Protection Program does not change your privacy settings, and Google collects vast amounts of information like location or search history that is in your best interests to disable.
Many options are located in your Google Account settings.
Disable, pause, and delete everything you can. If you use Android and other Google products like YouTube, it’s worth going over each service and product individually and reviewing the settings from there as well to make sure you didn’t miss any setting.
Android
Depending on your phone model, your technical skills, and your willingness to protect your privacy and security, you have several options available for you. At a minimum, any regular, unmodified Android phone with Google can be enrolled in the Advanced Protection Program outlined in the previous section. This automatically hardens your smartphone and blocks some common attack vectors like third-party Android applications. From that point onwards, you might not be able to install applications outside of the Google Play Store. This might represent an inconvenience to you depending on your use-case.
The second option is using a privacy and security oriented Android-based rom like LineageOS or, better yet, Graphene OS for Google Pixel phones.
There are possibly millions of different roms for different Android phones, and it would be impossible to list them all in this article, but a good starting point is to search on XDA Forums for your particular phone model. As usual, not all roms are created equal, and it is possible some roms are intentionally maliciously modified to undermine your privacy and security. For this reason, you should spend some time to research what you are going to put in your phone.
Additionally, Google apps might represent a threat to your privacy. It is possible to get roms without Google services, but you must understand that you might get reduced functionality like no push notifications or maps, even embedded maps in some applications. Thus, Google Apps or their lack thereof is a tradeoff you must assess at a personal level.
Apple
Apple offers a personal safety guide on their website. This guide is helpful for anyone, with any level of expertise, to be able to secure their Apple account, remove and review any unwanted information sharing (like location, or other updates). This will not help you safeguard any apps connected to your iCloud e-mail address, or installed on your iPhone, but it is an excellent first step.
Other resources
Please check out these guides:
They contain additional information including how to think about threat modelling and how to achieve a privacy-centric mindset.
Changelog
- Added “Other resources” section.